SecureMail
What is a Digital Certificate?
A Digital Certificate is a pair of electronic cryptographic keys that are used to encrypt/decrypt data. These keys are usually known as the public key and the private key. In normal operation, the public key is always made accessible to anyone, but the private key is only accessible by the owner.
Digital Certificates for email are similar to Web Server SSL Certificates used for online business transactions in the following ways:
It certifies that the email address belongs to the person who sends the email, similar to the case for SSL certificates where it certifies that the website belongs to a certain organization. It is used to encrypt the content of your email, similar to case where the data you transmit to a web server is encrypted with the SSL certificate.
What is a Digital Signature?
Digital Signature is an easy tool to let people know that: The email is sent by you and not someone who is trying to spoof your email address. The content of the email has not been tampered with during transmission. Due to the fact the email address can be spoofed, nobody can be sure as to whether a particular email does genuinely come from a particular person. When it comes to transmission of sensitive information, this becomes more important as the verification of the sender identity is paramount. You can use your digital certificate to sign your email digitally. The signature generated is thus referred to as the Digital Signature. Signing your email digitally does not mean to append your Outlook signature at the end of the email body text. It means that the content of the email is being calculated electronically to generate a hash that is unique to the message. This hash is then encrypted using the sender’s private key, and then appended with the original message and delivered to the recipient.
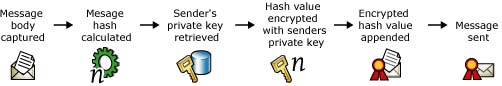
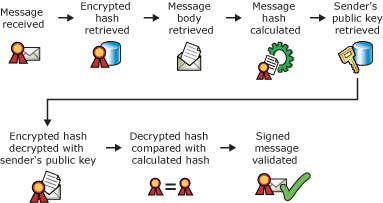
Upon receiving the email, the recipient can decrypt the hash using the sender’s public key and verify the authenticity of the email by re-generating the hash of the received email. If the received hash cannot be decrypted or if the received email content cannot be used to generate a hash identical to the received hash, this means that the mail content has been tampered with.
What is Email Encryption?
Digitally signing your email does not mean that your email is encrypted. Remember that only the hash is encrypted when sent along with the original message, so it is still possible for hackers to read the content of the email.
To ensure that the confidential mail content can only be read by the receiver (and of course the sender him/herself), the sender has to encrypt the message body, and doing so using his/her own private key as well as the recipient’s public key.
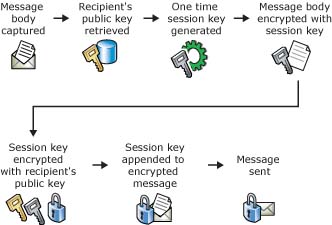
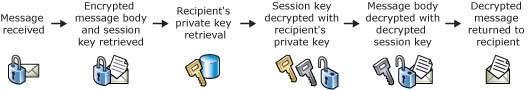
This way of encryption ensures that only the recipient can decrypt the email content using his/her private key, and therefore only the recipient will be able to read the content of the email.
That sounds pretty confusing, can you summarise what do I need?
The following diagram illustrates the requirements for email signing and encryption:
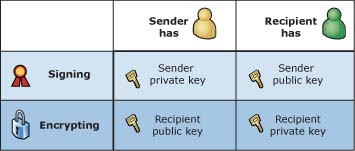
Basically:
For signing, the sender needs to have his/her own private key and the recipient needs to have the sender’s public key.
For encrypting, the sender needs to have the recipient’s public key while the recipient needs to have his/her own private key.

