Ongoing Ransomware Attack Incident Information Centre
NUS IT is investigating an ongoing ransomware attack incident that affects some of University’s systems and data. As part of our ongoing response to this incident, we created this page to share information and updates with NUS community.
Summary
(Last Updated: 29 August 2023)The ransomware infection was initially reported on 22 Aug 2023. Since then, additional systems have become infected and their data encrypted. As of 9:00am on August 29, 2023, a total of 23 systems have been compromised.
What is Ransomware?
Ransomware is a type of malicious software designed to deny user access to files by encrypting them using a key only known to the attacker. Payment is then demanded in exchange for the decryption key. This is typically requested in the form of a cryptocurrency, such as Bitcoin, to maintain anonymity and reduce traceability. Ransomware attacks can have potentially severe consequences for the University, as they may result in the loss of important data and the disruption of critical systems.
Ransomware attackers may also use a tactic known as double extortion. In addition to encrypting the victim’s files, they threaten to publicly release or sell sensitive data if the ransom is not paid. This tactic is increasingly common among ransomware attackers as it can be more effective at getting victims to pay the ransom.
Once infected with ransomware, the computer will show messages similar to the followings:
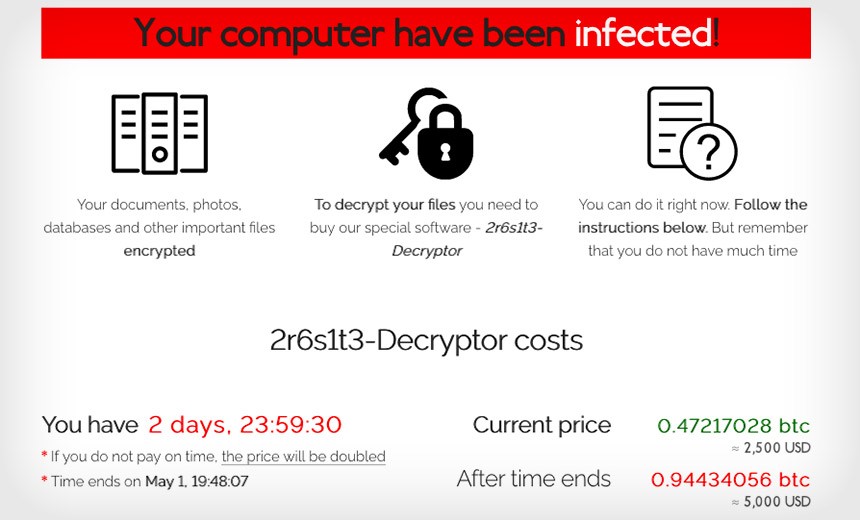
Caption: Sample of a locker ransomware message (REvil aka Sodinokibi)
What Should I Do if My Computer is Infected?
If you suspect that your computer has been infected with ransomware:
- – Disconnect your computer from WIFI and unplug the network cable. Ensure that your device is kept offline to prevent further spread of the Ransomware as well as transmission of data.
- – Further assess the extent of harm on your machine by checking if your files have been encrypted or made inaccessible. If confirmed, you should immediately email NUS IT at reportransomware@nus.edu.sg which is monitored 24*7, as well as report it at https://nusit.nus.edu.sg/its/cceforms/i-want-to/report-an-incident/, in accordance with NUS IT Security Policy.
- – If personal data is involved, you should also report the incident in accordance with the Personal Data Protection Policy & Procedures.
** IMPORTANT **
Staff or business units shall not liaise with the attacker on your own.
NUS does not condone the payment of ransom to ransomware attackers, whether in exchange for the decryption key of in response to double extortion, for the following reasons:
- Ransomware is a criminal enterprise, and paying the ransom will only embolden attackers to target more victims.
- There is no guarantee that attackers will provide the decryption key after paying the ransom.
- In a double extortion attack, there is no guarantee that attackers will not publicly disclose the stolen data even after paying the ransom.
In the event that critical data is irretrievable after a ransomware attack despite exhausting all possible means of recovery, and paying a ransom is deemed the only viable option, a deviation request must be sought as a last resort.
The deviation request must be submitted by the Department Head(s) of the affected business unit(s) to NUS President, with a copy sent to NUS CITO.
Other useful information:
- – As minimum protection on your computer device, make sure your anti-virus is active and up-to-date with the latest version.
- – Always diligently backup your files as a resilience measure to your data. You may check out these key articles on nBox or OneDrive via nTouch.
- – You may also check out some key information on ransomware response checklist at https://www.cisa.gov/stopransomware/ive-been-hit-ransomware

Let us all work together to secure NUS bIT by bIT.

